The introduction of Next Generation Firewalls has changed the dimension of management and configuration of firewalls, most of the well-known Firewall vendors have done a major revamp, be it the traditional command line mode or the GUI mode.
Palo Alto Networks is no different to many of those vendors, yet it is unique in terms of its WebUI. It’s a whole new experience when you access the WebUI of Palo Alto Networks Next-Generation Firewalls.
In order to start with an implementation of the Palo Alto Networks Next-Generation Firewalls one needs to configure them. Palo Alto Networks Next-Generation Firewalls can be accessed by either an out-of-band management port labelled as MGT or a Serial Console port (similar to Cisco devices). By using the MGT port, one can separate the management functions of the firewall from the data processing functions. All initial configurations must be performed either on out-of-band management interface or by using a serial console port. The serial port has default values of 9600-N-1 and a standard roll over cable can be used to connect to a serial port.

Figure 1. Palo Alto Networks Firewall PA-5020 Management & Console Port
By default, Palo Alto Networks Next-Generation Firewalls use MGT port to retrieve license information and update the threats and application signature, therefore it is imperative the MGT port has proper DNS settings configured and is able to access the internet.
To access the Palo Alto Networks Firewall for the first time through the MGT port, we need to connect a laptop to the MGT port using a straight-thru Ethernet cable. By default, the web gui interface is accessed through the following IP Address and login credentials (note they are in lower case):
- MGT Port IP Address: 192.168.1.1 /24
- Username: admin
- Password: admin
For security reasons it’s always recommended to change the default admin credentials. Until this condition is satisfied, the Palo Alto Networks Firewall alerts the administrator to change the default password every time he logs in, as shown in the screenshot below:
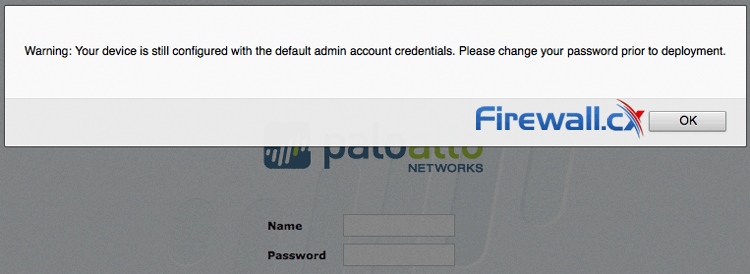
Figure 2. Palo Alto Networks Firewall alerts the administrator to change the default password
PERFORMING THE INITIAL SETUP IN PALO ALTO NETWORKS FIREWALL CHECK LIST
Below is a list of the most important initial setup tasks that should be performed on a Palo Alto Networks Firewall regardless of the model:
- Change the default login credentials
- Configure the management IP Address & managed services (https, ssh, icmp etc)
- Configure DNS & NTP Settings
- Register and Activate the Palo Alto Networks Firewall
Let’s take a look at each step in greater detail.
CHANGE THE DEFAULT LOGIN CREDENTIALS
Step 1: Establish connectivity with the Palo Alto Networks Firewall by connecting an Ethernet cable between the Management and the laptop’s Ethernet interface.
Step 2: Configure the laptop Ethernet interface with an IP address within the 192.168.1.0/24 network. Keep in mind that we’ll find the Palo Alto Networks Firewall at 192.168.1.1 so this IP must not be used.
Step 3: Open a web browser and navigate to the URL https://192.168.1.1 – Take note that this is an HTTPS site. At this point the Palo Alto Networks Firewall login page appears.
Step 4: Enter admin for both name and password fields.
Step 5: From the main menu, click Device > Administrators > admin
- Type the old password in the Old Password field
- Type the new password in the New Password field
- Type new password in the Confirm New Password field
- Click ok
CONFIGURE THE MANAGEMENT IP ADDRESS & MANAGEMENT SERVICES (HTTPS, SSH, ICMP)
At this point we have connectivity to the Palo Alto Networks Firewall and need to change the management IP address:
Step 1: Logon to the Palo Alto Networks Firewall using the new credentials entered in the previous section.
Step 2: From the web interface click Device > Setup > Management and select the Management Interface Settings radio button as shown below:
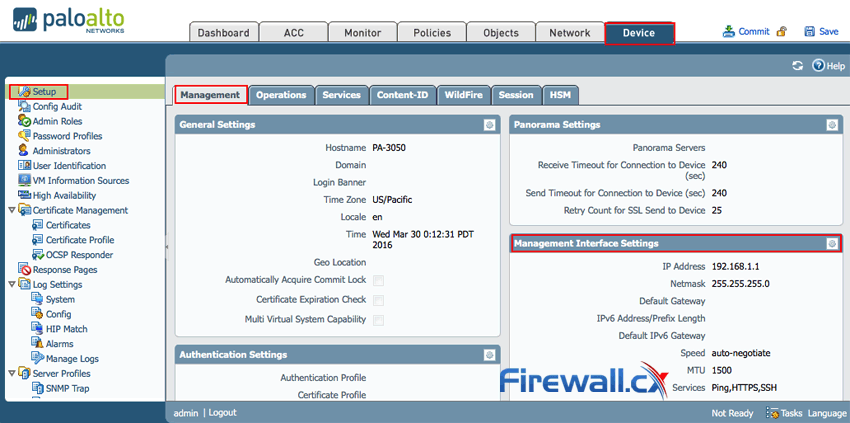
Figure 3. Accessing the Palo Alto Netowkrs Firewall Management IP Address tab
Next, change the IP Address accordingly and enable or disable any management services as required. HTTPS, SSH and Ping (ICMP) are enabled by default. When ready click ok:
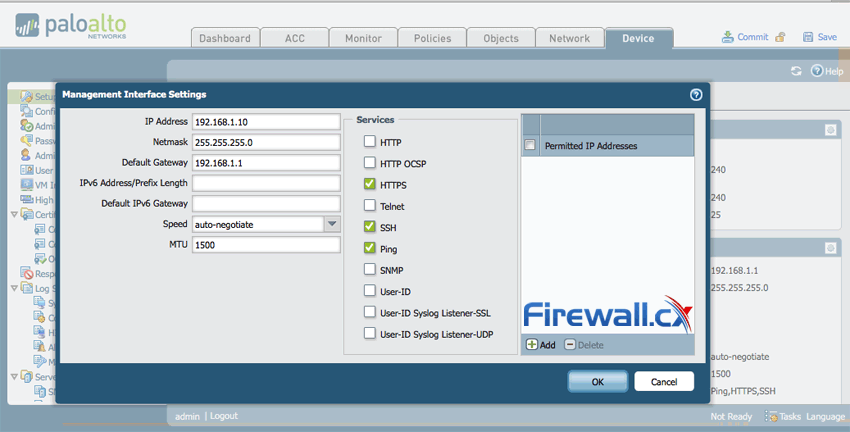
Figure 4. Changing the Management IP Address & services on the Palo Alto Networks Firewall
Step 3: Now click on Commit on the top right corner to save and commit the changes to the new configuration
CONFIGURE DNS & NTP SETTINGS IN PALO ALTO NETWORKS
This section assumes all previous steps have been completed and we are currently logged into the Palo Alto Networks Firewall web interface.
Step 1: From the menu, click Device > Setup > Services and configure the DNS Servers as required. When ready, click on OK:
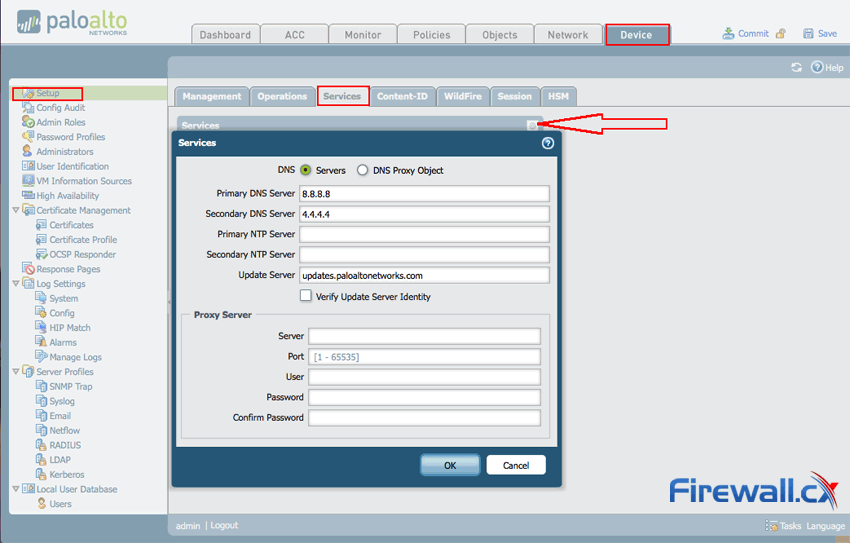
Figure 5. Configuring DNS Settings on Palo Alto Networks firewall
Step 2: Click on the Commit button on the top right corner to commit the new changes.
CONFIGURE MANAGEMENT IP ADDRESS, DEFAULT GATEWAY, DNS & NTP SETTINGS CLI (PAN-OS)
Similar to Cisco devices, Palo Alto Networks devices can be configured by web or CLI interface. While CLI interface tends to be slightly more challenging it does provides complete control of configuration options and extensive debugging capabilities.
This section shows how to configure your Palo Alto Networks firewall using the console port. The computer’s serial port must have the following settings to correctly connect and display data via the console port:
Step 1: Login to the device using the default credentials (admin / admin).
Step 2: Enter configuration mode by typing configure:
admin@PA-3050> configure
Step 3: Configure the IP address, subnet mask, default gateway and DNS Severs by using following PAN-OS CLI command in one line:
admin@PA-3050# set deviceconfig system ip-address 192.168.1.10 netmask 255.255.255.0 default-gateway 192.168.1.1 dns-setting servers primary 8.8.8.8 secondary 4.4.4.4
Step 4: Commit changes
admin@PA-3050# commit
REGISTERING AND ACTIVATING PALO ALTO NETWORKS FIREWALL
This section assumes all previous steps have been completed and we are currently logged into the Palo Alto Networks Firewall web interface.
Step 1: Click Dashboard and look for the serial information in the General Information Widget,
If the widget is not added, click on Widgets > Systems > General Information:
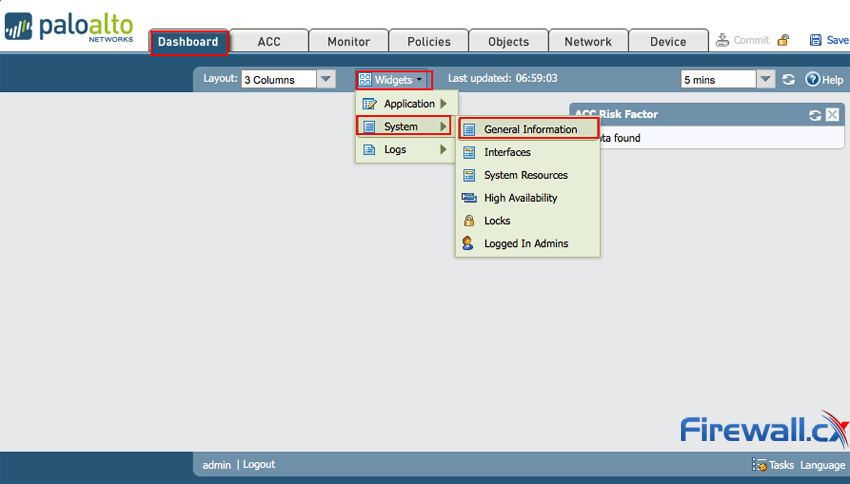
Figure 6. Adding Widgets to the Palo Alto Networks Firewall Web Interface
Step 2: Create a support account with Palo Alto Support.
Registering your Palo Alto Networks device is essential so you can receive product updates, firmware upgrades, support and much more.
First we need to create an account at https://support.paloaltonetworks.com and then proceed with the registration of our Palo Alto Networks Firewall device, during which we’ll need to provide the sales order number or customer ID, serial number of the device or authorization code provided by our Palo Alto Networks Authorized partner.
Further details about registration and activation process are available at Palo Alto Networks Live portal .
Step 3: Activate the license by clicking Device > License and select Activate feature using authorization code:
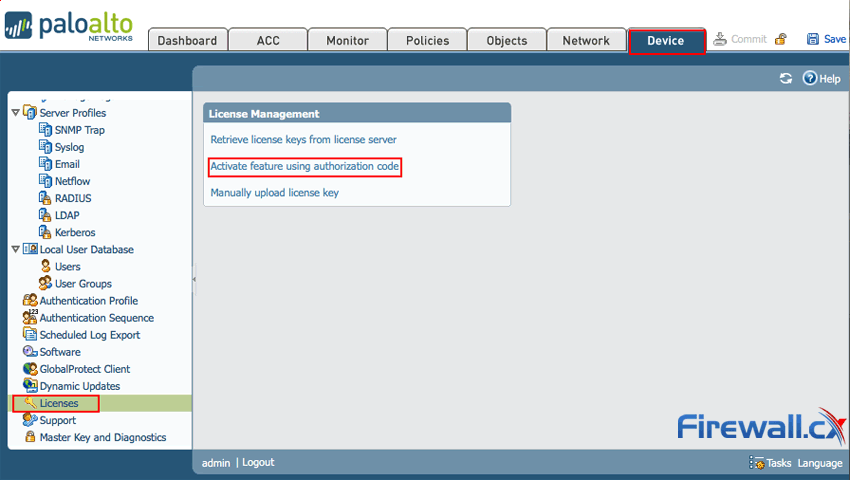
Figure 7. Activating the Palo Alto Networks Firewall license
When prompted, enter the Authorization Code and then click OK.
Finally, verify that the license was successfully activated.
Once the Palo Alto Networks Firewall is activated, it is ready for configuration according to our business’s needs.
This article showed how to configure your Palo Alto Networks Firewall via Web interface and Command Line Interface (CLI). We covered configuration of Management interface, enable/disable management services (https, ssh etc), configure DNS and NTP settings, register and activate the Palo Alto Networks Firewall.
No comments:
Post a Comment